автордың кітабын онлайн тегін оқу Английский для военных/Military English. Метод кейсов/Cases. Решения, ответы, словарь, глоссарий
Английский для военных/Military English. Метод кейсов/Cases
Решения, ответы, словарь, глоссарий
16+
Оглавление
- Английский для военных/Military English. Метод кейсов/Cases
- ПРЕДИСЛОВИЕ
- Как пользоваться данной книгой.
- Как пишутся кейсы
- PART 1
- Questions
- Solutions
- — WMD-E (Uncertain/High Threat)
- Answer
- CASE 2
- Practical Speaking Training. Сrush the fear of public speaking
- DRAW A CARTOON
- Vocabulary and Terminology Section
- BE-KNOW-DO
- PART 2
- WMD
- CASE NUMBER 3. NUCLEAR
- Questions
- Solutions
- CASE NUMBER 4. BIOLOGICAL
- Questions
- Develop and exercise a bio-attribution process
- WMD. KEY TERMS
- PART 3. TERRORISM
- TERRORISM
- General Rules
- Case 6. International Terrorism
- Profile of a Terrorist
- Questions
- Solutions
- Key Words and Terms
- Terrorism can be defined as
- Case 7. Lessons on terrorism
- the checklist
- Keys:
- Case 8. Eradicating terrorism
- Examine the possible solutions to eradicate terrorism
- Pirates
- PART 4 CYBER SECURITY ON MILITARY
- CASE NUMBER 9
- Operating Structure
- CASE NUMBER 10
- THE ATTACK OF HACKING
- What could an attacker learn from this information?
- What could an attacker learn from this information?
- Solutions
- Lesson
- MALWARE GLOSSARY
- Keylogger. Basically a form of spyware, a keylogger captures everything you type, including passwords and other sensitive information. Some keyloggers also capture screenshots, log your web browsing history, record anything copied to the clipboard, and more
- A-Z of computer and data security threats
- Whether you’re an IT professional, use a computer at work, or just browse the Internet, this book is for you. It explains the facts about threats to your computers and to your data in a simple, easy-to-understand language
- CASE NUMBER 11
- CYBER ATTACKS
- Solutions
- HACKING GLOSSARY
- CASE NUMBER 12
- SECURE PASSWORD
- Solutions
- CASE NUMBER 13
- THE SPIES INVENTED
- J=T, T=H & E=E
- J=T, T=H & E=E
- TU ESDGP THETE NTH
- D=D, G=A, P=Y
- Solutions
- What are some fun ways to encrypt a message?
- Step-by-step in pics
- THE AUTHOR
ПРЕДИСЛОВИЕ
.
Как пользоваться данной книгой.
4) выработки наилучшего решения.
Как пишутся кейсы
Задача коммуникативной методики — научить спонтанной речи на любые темы, и перестать переводить мысли с русского на иностранный язык. Коммуникативный подход, в общем и целом, предполагает изучение слов в контексте, без перевода на русский язык. И задача преподавателя не только научить Вас понимать, ЧТО означает слово, но и КАК его употреблять.
PART 1
Questions


Solutions

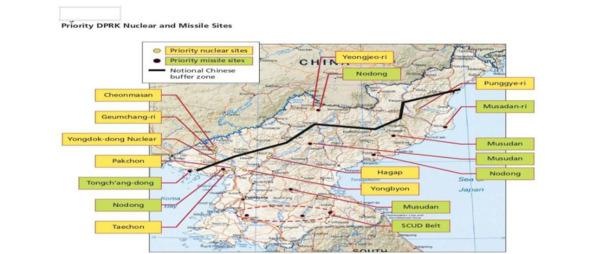

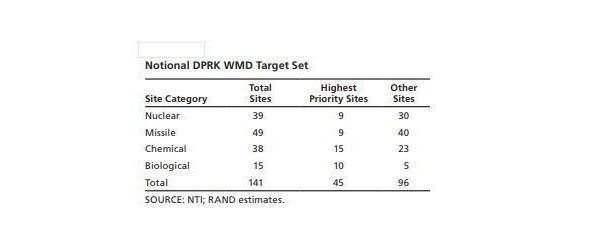
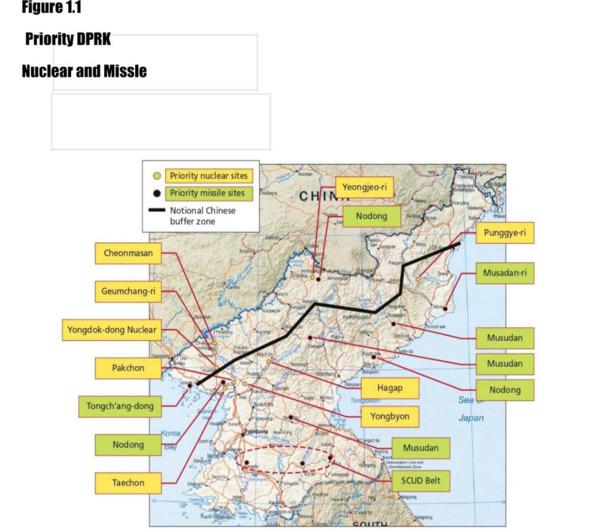
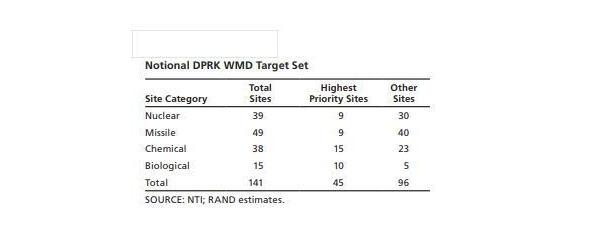
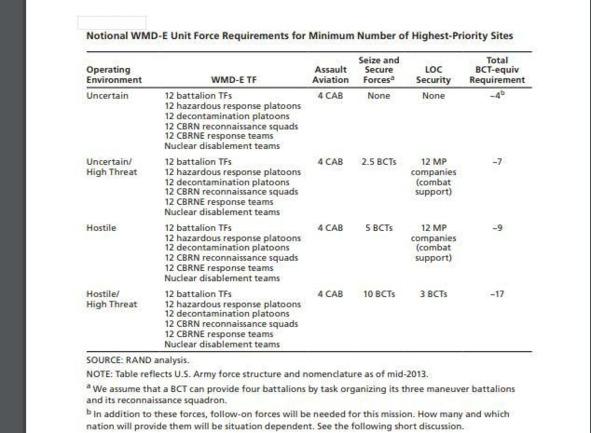
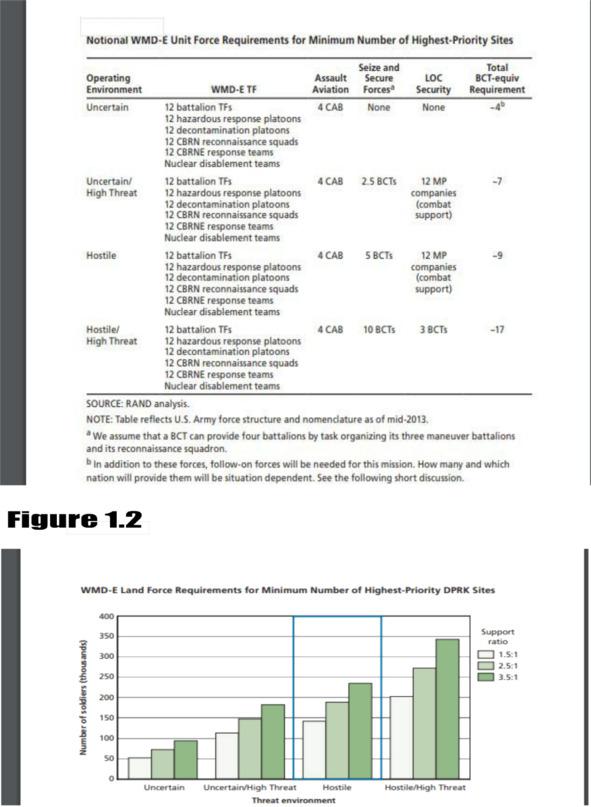
— WMD-E (Uncertain): This environment features a low threat level — consistent with the collapse of the DPRK regime and complete disintegration of the military. This might occur if a power struggle within the Kim regime resulted in open fighting that pushes an already dangerously unstable economy and society into chaos and collapse.
